Why SBOMs Are Not One-and-Done 📦🔄
2025-05-04
Jason Smith
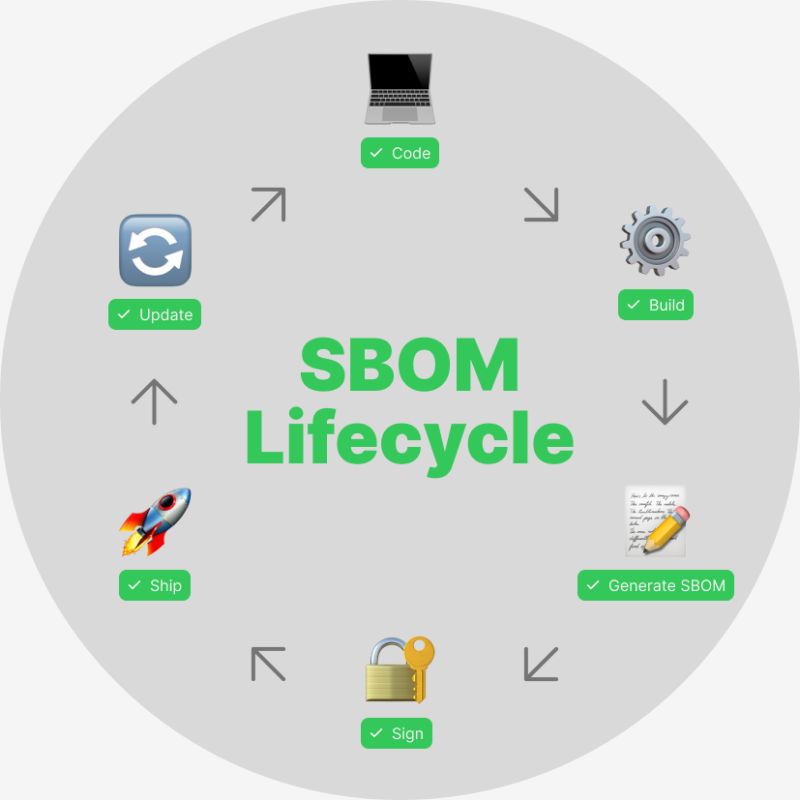
✅ You’ve generated an SBOM. Congratulations!
But here’s the truth. An SBOM is not a report you create once and tuck away. Modern software changes constantly. New features, updated libraries, security patches, refactored code… All of this reshapes your software supply chain.
That means your SBOM must evolve alongside your software. Here’s why a one-and-done SBOM isn’t enough:
🔄 Continuous delivery = continuous change
- Your software isn’t static. Your SBOM can’t be static either.
⚠️ New risks appear every day
- A library that was safe last month might have a critical vulnerability today.
📊 Compliance requirements keep shifting
- Regulators, customers, and partners increasingly expect current SBOMs, not historical snapshots.
🔐 Trust is only as strong as verification
- It’s not enough to just have an SBOM. You need to be able to prove it’s authentic. Signing SBOMs and using cryptographic verification ensures they haven’t been tampered with.
🏗️ Automation is key
- To keep up, SBOM generation needs to be integrated into your CI/CD pipelines - not left as a manual task.
Key takeaway:
If you’re not updating your SBOM regularly, you’re not really managing your software supply chain. And let’s be honest, if you don’t have your SBOM generation automated it is already out of date.
Are you automating SBOM generation or piecing it together manually? Are you signing them? What’s worked (or hasn’t worked) for your team?
If this or any of my past SBOM posts have resonated, drop a comment, I’d love to hear what you think!! 💬👇
#SBOM #CyberSecurity #SoftwareSupplyChain #DevSecOps #OpenSourceSecurity #SupplyChainSecurity #ContinuousDelivery #DigitalTrust #SoftwareIntegrity #SecureDevelopment