🔏 SBOM Signing ≠ Security
2025-06-08
Jason Smith
Just because an SBOM is signed doesn’t mean it’s safe.
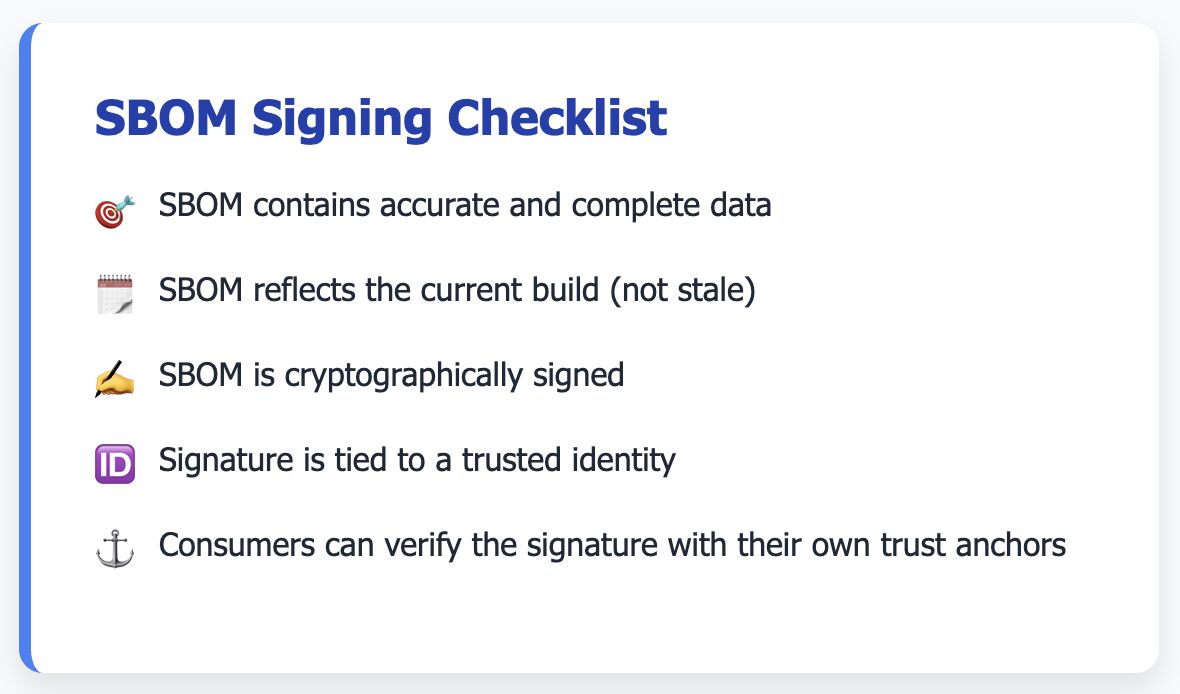
Signing is still important though. It gives you integrity. You know the SBOM wasn’t tampered with after it was produced.
But integrity ≠ trustworthiness.
Here’s why:
🧱 Garbage In, Garbage Out
If the SBOM was generated incorrectly, with missing or outdated components, signing it just seals in the errors.
🎭 Signed ≠ Honest
A signature only tells you who signed the SBOM. It says nothing about whether they were truthful, competent, or even authorized to sign it.
📅 Is It Still Current?
Software changes fast. An SBOM signed last week may already be outdated. If you can’t link the SBOM to a specific build artifact or verify it’s up to date, the signature alone doesn’t help.
⚖️ Trust is Contextual
Do you trust the signer? Are they using your keys, their own, or a third-party authority? Just because something can be verified doesn’t mean you’ll trust what it says.
✅ Signing is a Baseline, Not a Guarantee
Think of signing as the “tamper-evident seal”. Useful, but only meaningful if the package was accurate, complete, and fresh when sealed.
🤔 The takeaway?
Signed SBOMs are better than unsigned ones. But we need complete, current, and verifiable SBOMs, ideally linked to build systems and verified by trusted parties.
💬👇 Would love to hear:
❓ How are you validating SBOM accuracy and provenance today?
❓ Does signing increase your trust?
❓ What else would increase your trust?
#SBOM #SoftwareSecurity #SupplyChainSecurity #DigitalSignatures #SecureDevelopment #DevSecOps #ApplicationSecurity #SoftwareIntegrity #CyberSecurity