𝗪𝗵𝗼 𝗮𝗰𝘁𝘂𝗮𝗹𝗹𝘆 𝗯𝘂𝗶𝗹𝗱𝘀 𝗦𝗕𝗢𝗠𝘀? 𝗔𝗻𝗱 𝘄𝗵𝗼 𝗻𝗲𝗲𝗱𝘀 𝘁𝗵𝗲𝗺? 🤔🔍
2025-05-18
Jason Smith
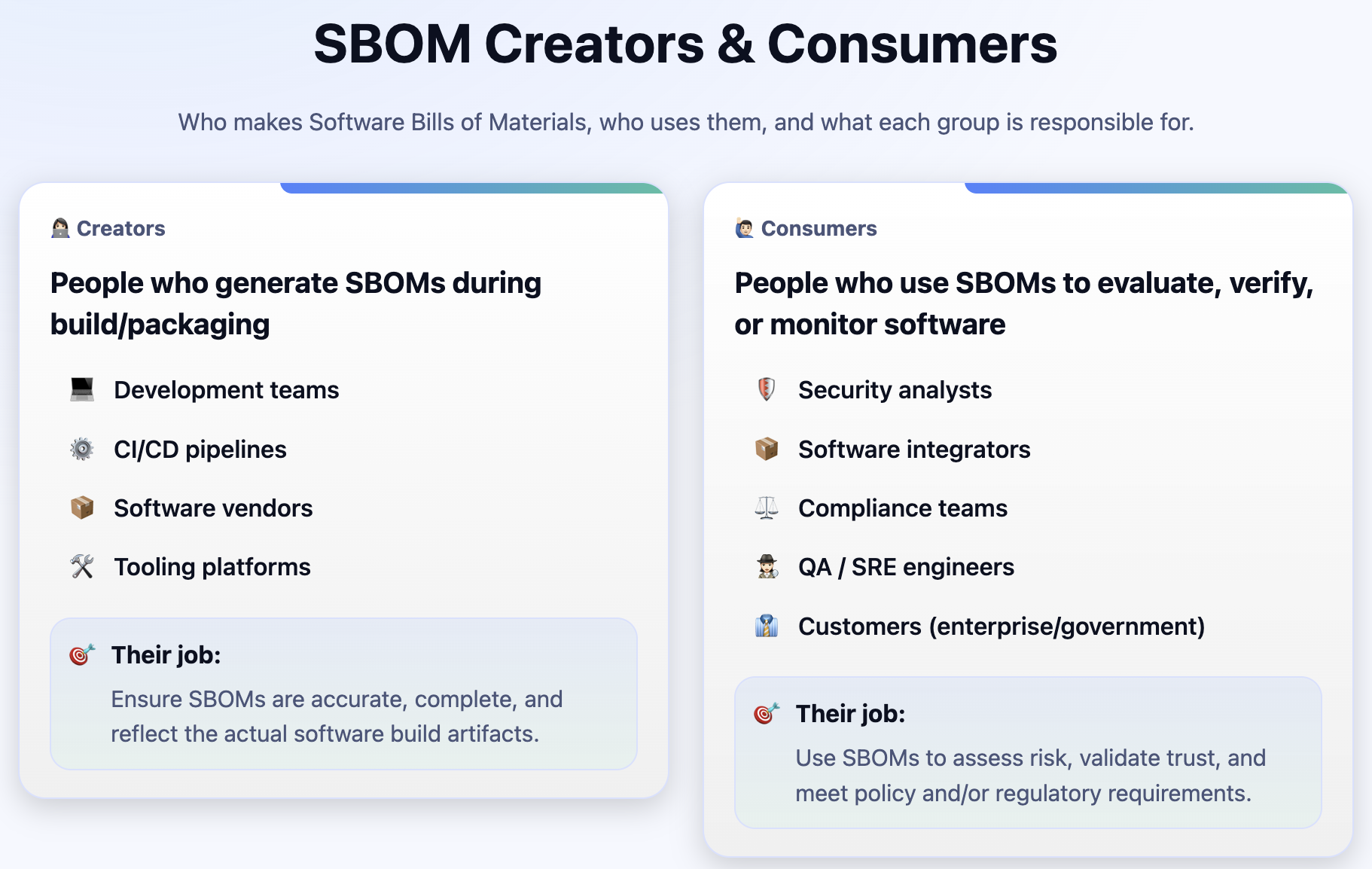
SBOMs are a critical tool for understanding your software supply chain. But not everyone touches an SBOM the same way.
There are 𝗰𝗿𝗲𝗮𝘁𝗼𝗿𝘀 and there are 𝗰𝗼𝗻𝘀𝘂𝗺𝗲𝗿𝘀. Sometimes they’re the same person, but often they’re not.
👩🏻💻 𝗖𝗿𝗲𝗮𝘁𝗼𝗿𝘀
These folks generate SBOMs as part of the software build or packaging process:
- 💻 Development teams
- ⚙️ CI/CD pipelines
- 📦 Software vendors
- 🛠️ Tooling platforms
🎯 Their job: Ensure SBOMs are accurate, complete and reflect the actual software build artifacts.
🙋🏻♂️ 𝗖𝗼𝗻𝘀𝘂𝗺𝗲𝗿𝘀
These folks use SBOMs to evaluate, verify, or monitor software:
- 🛡️ Security analysts
- 📦 Software integrators
- ⚖️ Compliance teams
- 🕵🏻♀️ QA / SRE engineers
- 👔 Customers (especially enterprise/government)
🎯 Their job: Use SBOMs to assess risk, validate trust, and meet policy and/or regulatory requirements.
🤓 𝗛𝗲𝗿𝗲’𝘀 𝘄𝗵𝗲𝗿𝗲 𝗶𝘁 𝗴𝗲𝘁𝘀 𝗶𝗻𝘁𝗲𝗿𝗲𝘀𝘁𝗶𝗻𝗴…
If you’re a 𝗰𝗿𝗲𝗮𝘁𝗼𝗿, you’re responsible for 𝘁𝗿𝘂𝘁𝗵.
If you’re a 𝗰𝗼𝗻𝘀𝘂𝗺𝗲𝗿, you’re responsible for 𝘁𝗿𝘂𝘀𝘁.
This is why signing SBOMs and supporting cryptographic digital verification is critical. Without that, you might be consuming… misinformation? 🤷♂️
SBOMs aren’t just build-time artifacts. They are communication tools across the software lifecycle. 💻🔄
Are you generating SBOMs today? Or consuming them from vendors? Do you know if they are trustworthy? 🤔
#SBOM #SupplyChainSecurity #CyberSecurity #SecureSoftware #OpenSourceSecurity #DevSecOps #DigitalTrust #SoftwareIntegrity #Compliance #SoftwareSupplyChain #BuildSecurityIn