What's Inside an SBOM? 🧠
2025-05-11
Jason Smith
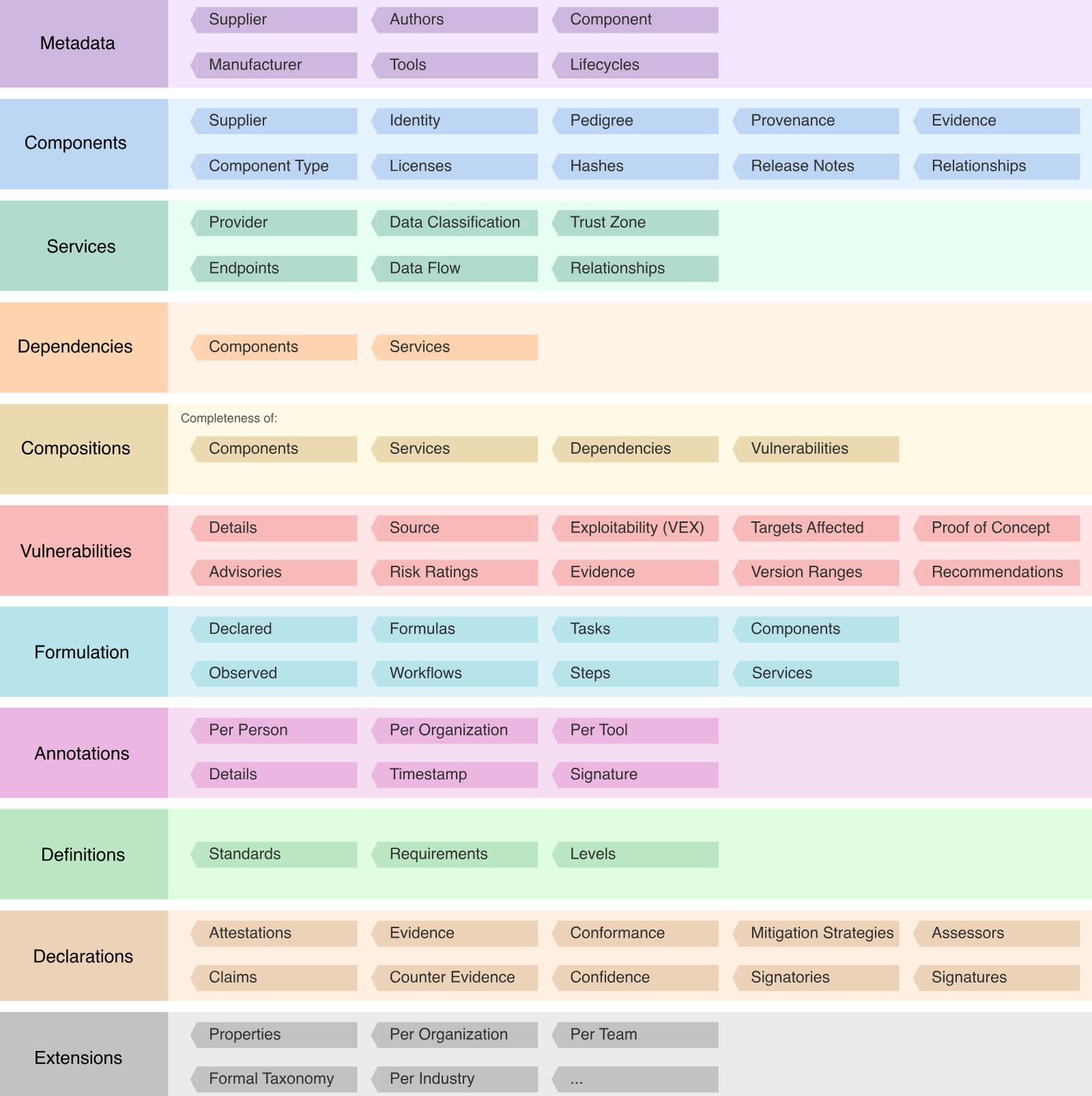
(Image sourced from OWASP CycloneDX SBOM/xBOM Standard) - https://cyclonedx.org/specification/overview/
A Software Bill of Materials (SBOM) is more than just a list of libraries - it’s a structured, detailed map of what makes up your software. 💻
But not all SBOMs are created equal. Some are like handwritten grocery lists. 📝 Others? Like detailed warehouse inventory sheets. 📋🏭
So what goes in a useful SBOM? 🤔
Core Components:
- 📦 Component name
- #️⃣ Version number
- 🆔 Unique identifier
- 🔗 Source or download location
- 📜 License type
Metadata for Lifecycle:
- 🧑 Who created the SBOM
- 🕒 When it was generated
- 🔧 What tools created it
- 🏷️ What product or build it refers to
A well-formed SBOM also helps to strengthen security enabling you to:
- 🔍 Detect vulnerabilities
- 🚨 Respond quickly to incidents
- 📜 Verify open-source license compliance
- 🛡️ Build trust across your software supply chain
And here’s the kicker - just having an SBOM isn’t enough. You also need to know:
- 🤔 Can you trust it?
- 🕵 Has it been tampered with?
- 💎 Is it authentic?
That’s where digital signatures, hashing, and attestations come in — helping prove who created the SBOM, what build it came from, and that it hasn’t been altered in transit. 🔐
Because in security, trust must be earned and verifiable. 🤝
#SBOM #CyberSecurity #SoftwareDevelopment #SupplyChainSecurity #DevSecOps #OpenSourceSecurity #SoftwareSupplyChain #SoftwareTransparency #DigitalTrust #SecureDevelopment #SBOMAnatomy #SoftwareIntegrity 💾🔐