Blog

I’ve been diving into the EN...
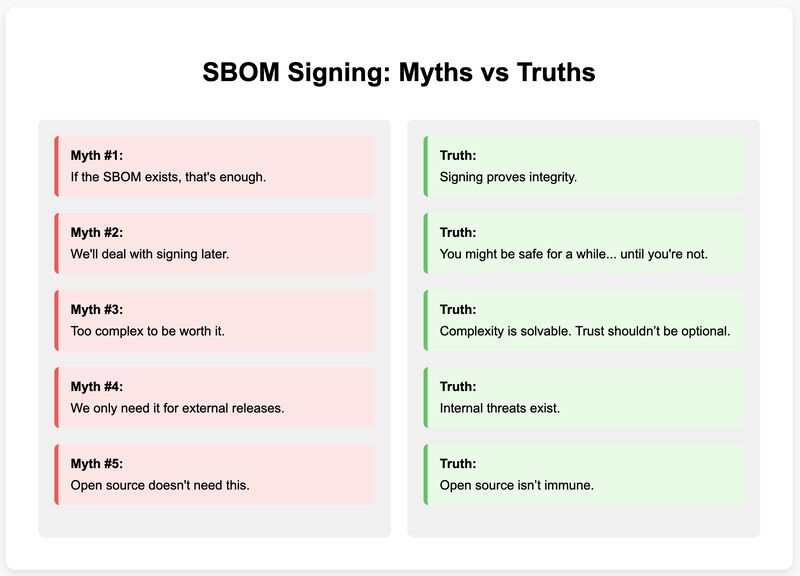
“If the SBOM exists, that’s enough” “We’ll deal with signing later” “To...
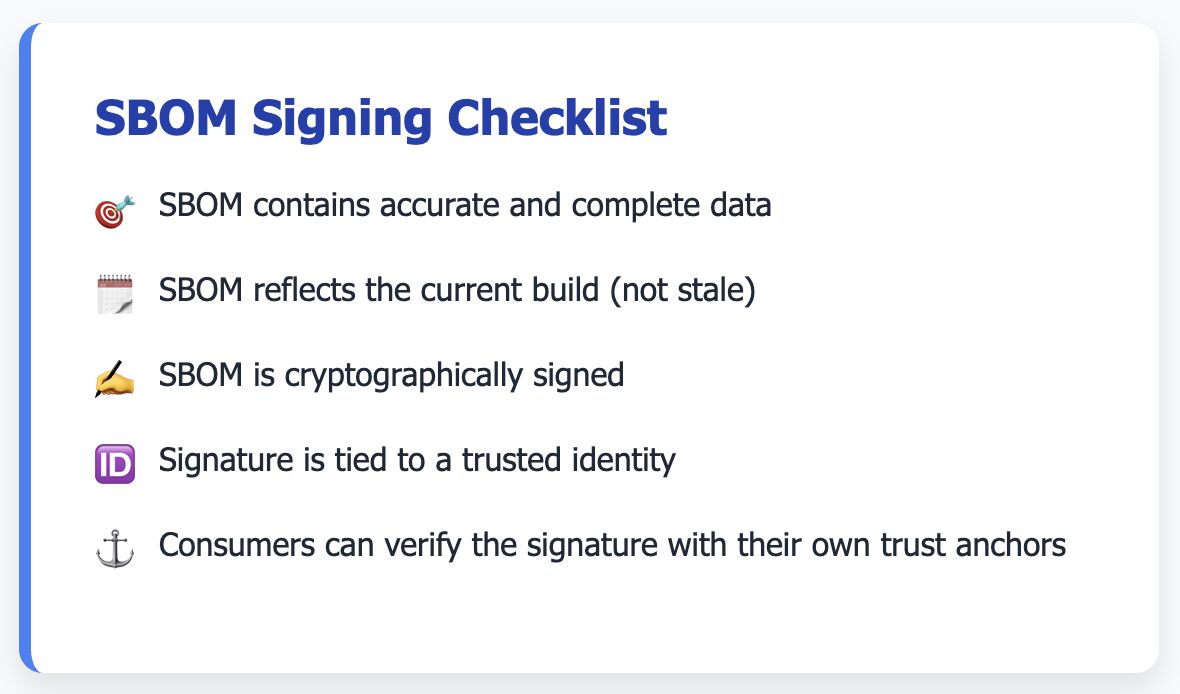
Just because an SBOM is signed doesn’t mean it’s safe. Signing is still important though. It gives you integ...
Enterprise-grade cryptographic signing and validation for every SBOM you produce or consume.
Native support for CycloneDX signatures and detached SPDX verification, ensuring interoperability across ecosystems.
Multi-tenant, compliance-ready design that scales to regulated industries and large organizations
API-first design enables easy drop-in integration with existing DevSecOps pipelines (GitHub, GitLab, Jenkins, Bitbucket).
Support for Hardware Security Modules to protect signing keys in any environment.
Perform signing and verification in air-gapped or highly regulated environments with full offline support.

I’ve been diving into the EN...

“If the SBOM exists, that’s enough” “We’ll deal with signing later” “To...

Just because an SBOM is signed doesn’t mean it’s safe. Signing is still important though. It gives you integ...