Posts

Stop Signing the Container 📦, Start Signing the Content
In my current work with the OpenSSF SBOM...

The Binary Blob Trap in SBOM Signing 🪤
Is the industry’s favourite SBOM signing tool actually creating a verific...

Thoughts on ENISA's New SBOM Implementation Guide 🤔
I’ve been diving into the EN...
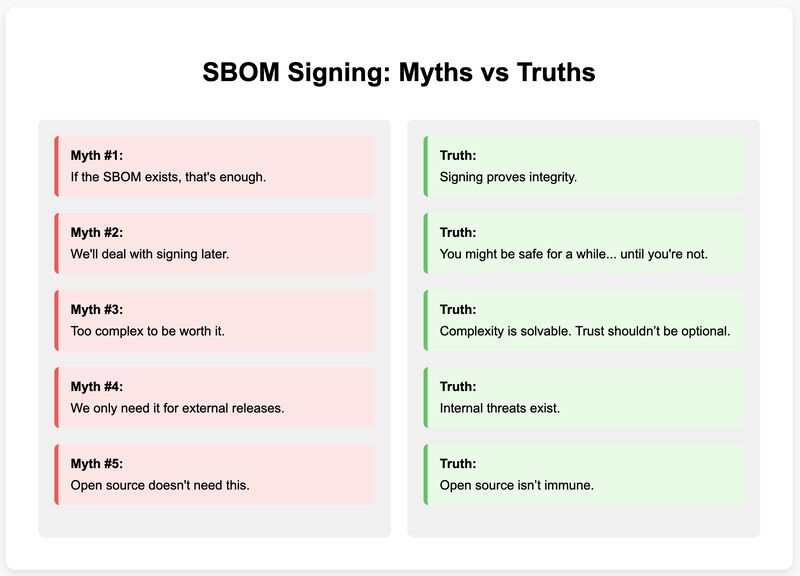
🚨 SBOM Signing: The Myths That Are Putting You at Risk 🔥
“If the SBOM exists, that’s enough” “We’ll deal with signing later” “To...
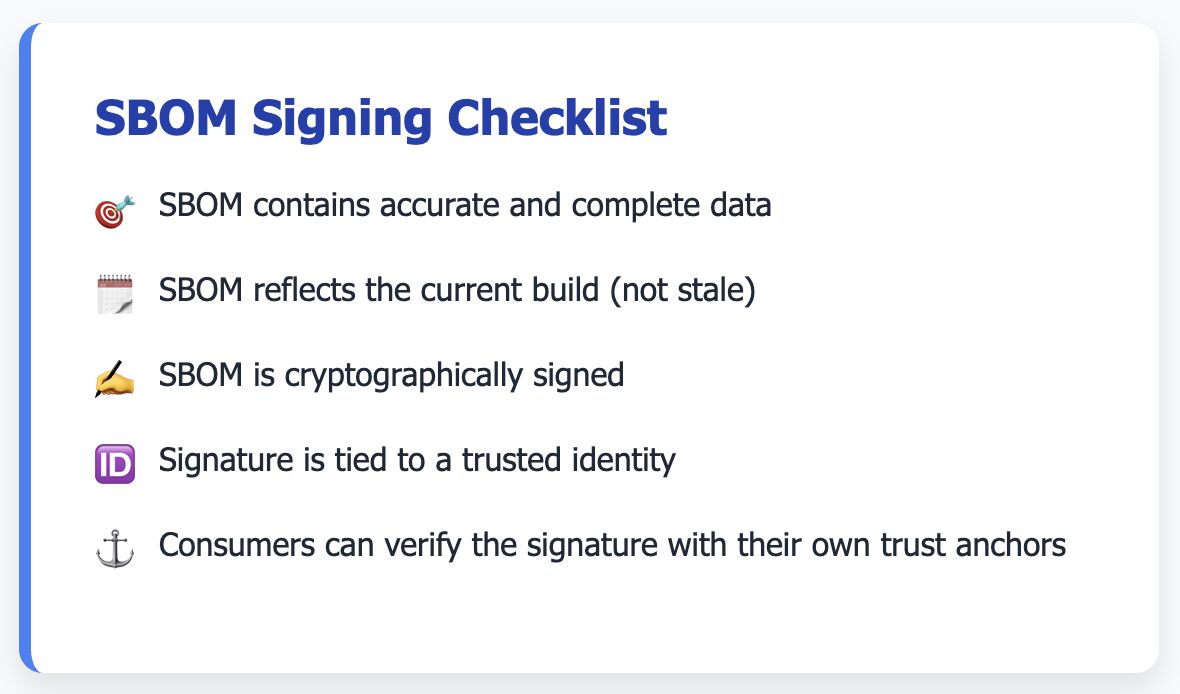
🔏 SBOM Signing ≠ Security
Just because an SBOM is signed doesn’t mean it’s safe. Signing is still important though. It gives you integ...

The Evolution of SBOMs at OwnersBox
I gave a presentation at the CISA SBOM Community Weekly Meeting yesterday where I shared how we approached SBOMs in my latest r...